Go
However, we often do not realize that acquiring information about friends works both ways.
Źródło: via Kaspersky Lab PolskaSomeone else can use the same tools, the same portal or search engine to find information about us.What guarantee we have that such a person will be guided - as in our case - ordinary curiosity?Sometimes it is worth asking yourself - how much can you learn about me from the Internet?
Stalking is not only phones at 3 am
A very loud matter, which can undoubtedly be included in the harassment, was notorious calling and interfering in the private life of the leader of the Linkin Park group, Chester Bennington.Devon Towsend has gained access to the private mailbox and telephone post of the team's frontman.This allowed her to learn about the detailed schedule of Chester's day and his family.The woman also quickly obtained insight into photos and family notes kept on the e-mail inbox.She also changed access passwords to various services.The Benningotons were also disturbed by phones at very early hours, third and four in the morning.After a long time, the perpetrator of all these incidents managed to stop.As it turned out, the woman did not have any hacker skills that would allow her to break the e -mail security.The slogan was so simple that she managed to guess it.
Everyone can fall victim to a cyberstalker and it depends on us how much he can afford
Just harassment does not necessarily have to be notorious e -mail writing or - in general - attempts to make contact with the victim.It can also be theft of identity and using it to compromise the victim, e.g. by placing offensive and abusive comments on websites or photos to humiliate someone.This type of action very quickly reflects on the balance of the victim/victim.This problem especially applies to young people in school age.Once given by the peer environment, the negative patch is heavy to remove, even in the face of evidence testifying to the innocence of the victim of Stalker.The lie begins to live with its own rhythm, increasingly affecting the victim's psyche, which without proper help can go to his life in extreme cases.
You are not on "Facebook" - you do not exist
If 2-3 years ago, they asked a statistical Polish Internet user, where you can find the most information about people, the our-class social networking site would certainly be mentioned in a leading position.Today, it would be like Facebook, but this does not change the fact that we often treat websites of this type as a gigantic database that users update on an ongoing basis, thanks to which it contains the latest data.
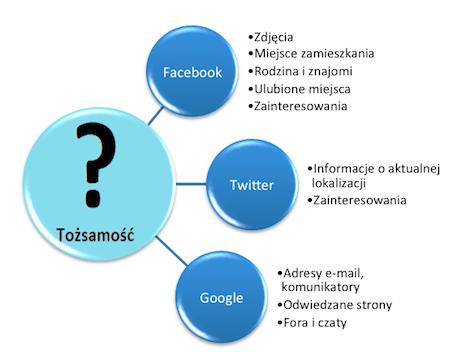
Even seemingly insignificant information can lead to a different one, creating a network of connections and shaping the profile of the person with whom Stalker tries to make contact.You do not need to place all data about yourself in one place to become a victim of surveillance.Sometimes finding an e -mail address and a properly constructed query in the Google search engine will lead to a page where the messenger number will appear next to the address.Following this track, it may turn out that in the past the victim issued, for example, an online advertisement about the sale of an item, where the said messenger and telephone number gave contact.This is how you can gather a lot of information.However, no one will deny that social networks are the largest mine of knowledge.
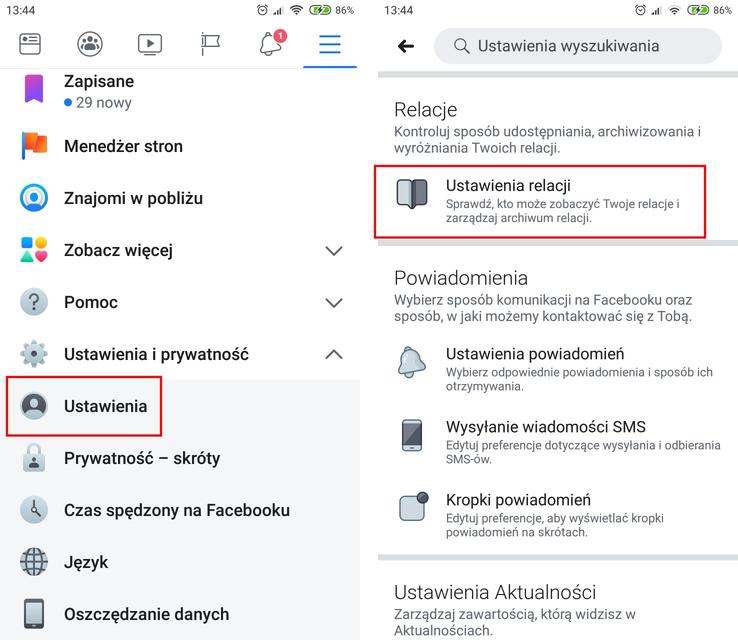
Źródło: Informacje, jakie można uzyskać na temat drugiej osoby tylko przy pomocy internetu (fot. Materiały prasowe)All entries and photos can be public and available to every Facebook user, we can also limit ourselves to friends, friends or ourselves.In the theory of Cyberstalker, he can only obtain information about us if you choose the first option, and thus public data sharing.In practice, however, it looks a little different.This is well illustrated by the figure below:
Źródło: Schemat pozyskiwania informacji przez cyberstalkera w zależności od ustawień facebookowego profilu pokrzywdzonego (fot. Kaspersky Lab)Aequitas sequitur legem - Justice follows the law
During the conference "Network attacks - IT, LAW, Electronic Evidence" organized by the Student Scientific Association of New Technology Law, which took place in December 201. At the Faculty of Law and Administration of the Nicolaus Copernicus University in Toruń, Mrs. Beata Marek touched the problem of cyberstalking in termslegal, supporting with this specific examples.It is clear that the legislator takes into account new technologies and supports Internet users creating appropriate regulations.In the Polish Penal Code, the phenomenon of stalking was regulated by the legislator in Article 190A:
_ § 1. Who, by persistent harassment of another person or the closest person, raises his sense of danger, or significantly violates his privacy, is subject to the penalty of deprivation of liberty for up to 3 years old
_ § 2. The same punishment is subject to who, impersonating another person, uses her image or other personal data to cause her property or personal damage._
_ § 3. If the consequence of the act specified in § 1 or 2 is the hatch of the victim for his own life, the perpetrator shall be punishable by imprisonment from a year to 10 years.
_ § 4. The prosecution of the crime specified in § 1 or 2 takes place at the request of the victim._
Unlike the cases of harassment in the real world, Cyberstalker leaves many more evidence that may be the basis for convicting him.Behavior by the victim/victim of logs, news archive, emails, SMSs or biling indicating a persistent desire for a stalker to contact a stalker allows for faster guilt and the use of one of the above-mentioned paragraphs.
It is very important that the law regulates such important issues as harassment, especially in the era of cyberspace, where millions of people communicate with each other using their real names and other personal data.Nevertheless, even the most severe recipes are not able to fully protect against cyberstalkers.One of the functions of criminal law is scaring before committing a crime, but exacerbation of regulations does not always go hand in hand with a reduction in crime, and history has often given evidence.Prevention and publicizing this phenomenon are equally important.It would be wrong to say that the victims are guilty of themselves because they put too much information about themselves on the internet.Many people do this because they simply can't predict the effects of such behavior.
The mentioned conference in Toruń describes one particularly drastic case of cyberstalking.It was a description of the situation in which the persecuted person could not cope with growing pressure, the consequence of which was to take his own life.It all began with letting the network to the network embarrassing to the victim of photos, as well as impersonating her name.These types of events are the most clear example of how much a cyberstalker can affect the lives of another person and literally ruin them overnight.
Summary
Everyone can fall victim to a cyberstalker and it depends on us how much he can afford. Umieszczanie prywatnych zdjęć z dostępem publicznym, poczucie anonimowości w sieci i nieprzewidywanie konsekwencji niektórych działań może doprowadzić nas do punktu, w którym osoby trzecie będą w stanie nas nękać i to nie siląc się przy tym na sztuczki hakerskie. Pewne jest to, że nękanie w sieci to coraz częściej spotykane zjawisko i należy z nim walczyć. O dowody przemawiające na niekorzyść cyberstalkera jest dużo łatwiej niż w realnym świecie, ponieważ maile czy zapisy rozmów prowadzonych przy pomocy komunikatora są namacalnym świadectwem działalności prześladowcy. Osoby, które spotkały się z tym problemem powinny pamiętać, że nie są same i istnieje wiele organizacji, które pomagają nie tylko zwalczać cyberstalking, ale - co ważniejsze - udzielają wsparcia, zarówno od strony prawnej, jak i psychologicznej.
Source: Kaspersky Lab
Antivirus programs and security!
Oceń jakość naszego artykułu:Twoja opinia pozwala nam tworzyć lepsze treści.Share the opinion
Stay with us on a regular basis
on Instagram
👍Lubię to!on Facebook
Comments
Trwa ładowanie...